It used to be that the most intrusive experience business travelers faced at airport security was a possible pat-down, or a customs check of luggage.
These days, border control agents are searching passengers’ phones, tablets and laptops for … well, anything they want to see. Your complying with the request grants them access to documents, emails, passwords, contacts and social media account information. So travelers carrying confidential or privileged corporate information (in addition to the merely personal) need to take steps ahead of time to ensure that private data stays private.
The laws around data privacy at checkpoints are murky, and border control officers in the U.S. and elsewhere have been making full use of the allowable gray areas, asking travelers to turn over email logins and social media passwords, searching devices and making forensic copies of data. If this concerns you and your company, these tips could prove useful. While legal issues vary by country, most of these suggestions will provide a measure of data security in a variety of situations.
This the final part of a three-part series: The first offered tips and advice for Apple devices (macOS laptops, iPhones and iPads) and Part 2 covered Android devices. Here, we focus on traveling with Windows laptops.
This advice primarily applies to devices running Windows 10, but most of these tips are relevant to Windows 7 and 8 as well. Techniques are listed roughly in order of least to most complex, which is also generally in increasing degree of protection provided. If you are traveling with a corporate laptop, you may need to coordinate with your IT staff to determine which options are appropriate and available to you.
1. Turn off your device
The first and easiest step — this applies to all devices, not just Windows — is to make certain that all electronic devices are powered down completely before you get to the border. The two main reasons to do so: In some cases, the legal bar is higher to ask a traveler to turn on a device that is off than it is to simply wake one from standby or sleep mode. It may seem an odd distinction, but it has proved a critical one in some cases. The second, more compelling reason to power down your Windows devices is that if you have encrypted some or all of your laptop drive (see details below), most encryption mechanisms provide far better security from data searches if the encrypted device is off. This won’t help you if you comply with a request to power on and log into your device, but some of the steps described below will help in those scenarios as well.
2. Require a passcode
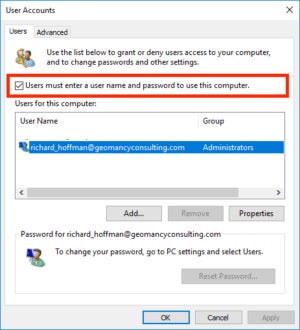
Always require a passcode to access your device, and make sure the passcode is required by default anytime your laptop is powered on, or awakened from sleep. If you have disabled the requirement to enter a passcode at startup, re-enable it. (Follow the instructions here, in reverse — go into the netplwiz program, and make sure “Users must enter a user name and password to use this computer” is checked.)
 Microsoft
Microsoft
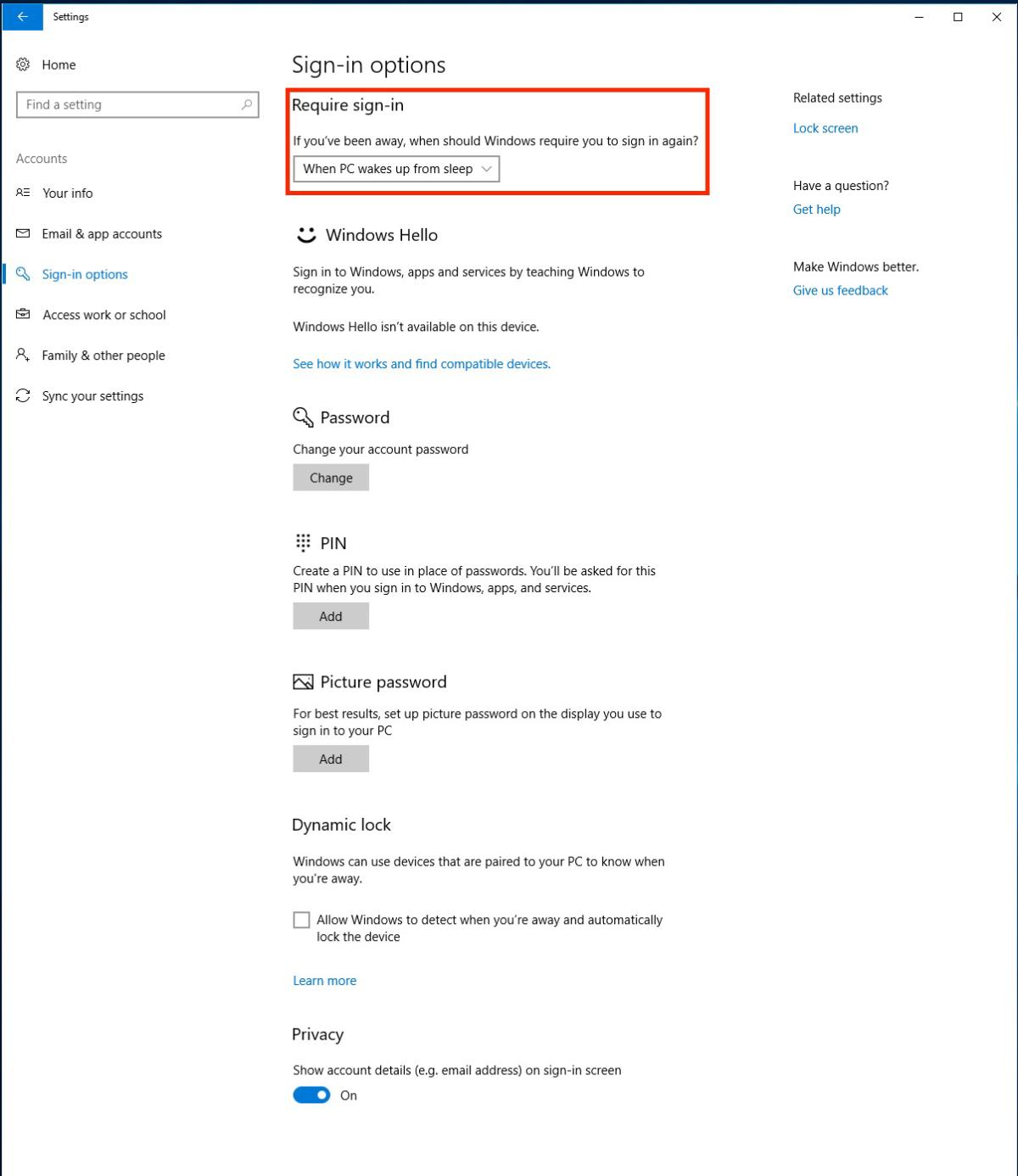
Next, make sure that your laptop requires a password upon wake from sleep — for Windows 10, this option used to be in the Power Options window in the Control Panel, but for current versions it can be found in the Settings application. Go to Settings > Accounts > Sign-in options, and make sure the answer to the “If you have been away, when should Windows require you to sign in again?” dropdown selection is “When PC wakes up from sleep.” There’s more complete information here.
For Windows 7, the option to turn this on is still under Power Options.
If you have a laptop with biometric authentication (fingerprint or iris scan), accessed via Windows Hello, you should consider turning this off before you travel. Among the odd legal gray areas are some scenarios where you could be compelled to unlock your devices with a fingerprint or other biometric authentication, even if you wouldn’t be required to surrender a password.
These options are under Settings > Accounts > Sign-in options. If Windows Hello is in use, you can select Remove here. More information on turning Windows Hello on and off is available here.
It is also potentially a good idea to turn off the ability to use Cortana while your device is locked. As of the Windows 10 Anniversary Update, you may find that Cortana is enabled by default on your lock screen, no matter what your previous settings were. This option can be found under Settings > Use Cortana even when my device is locked.
3. Clean out your browser cache
Clear your browser cache data: for Microsoft Edge, this option is found under Hub > History, then select “Clear all history,” select the types of data you want to delete, and choose “Clear.” You can also delete your browsing history from Cortana by selecting “Change what Microsoft Edge knows about me in the cloud,” and “Clear browsing history.”
If you’re still using Internet Explorer, you can delete your browsing history under Tools > Safety > Delete browsing history.
For Chrome, enter Chrome and from the browser toolbar select Menu > More Tools > Clear Browsing Data, select the checkboxes for all data you want to delete, choose “Beginning of time” to delete everything, and select “Clear browsing data.” More detailed information from Google can be found here.
Finally, for Firefox users, the current version of Firefox has a handy “Forget” button you can set up for easy use. But you can also go through and delete your cache and other saved information in the same way as the other browsers, from the Menu button > History > Clear Recent History. Select the type of information and date range, and select Clear Now. More info here.
4. Encrypt your data
This security option can protect you not only from having information taken and used if your laptop is stolen, but also to some extent from having data on your hard drive easily copied when crossing the border. If you want truly secure encryption, there are third-party options — however, the built-in Windows BitLocker feature protects your data from most access attempts and is a good option to enable when traveling. Unfortunately, the built-in encryption situation with Windows can be … messy, especially with older devices. In all honesty, if you’re doing this on your own device, you’ll likely have an easier time with a Mac or Chromebook. If you have IT support, or are a more advanced user, it is possible to lock down a Windows laptop, and enabling BitLocker is one of the recommended steps.
Note: BitLocker encryption is only available on Windows 10 Pro, Education and Enterprise editions. And for Windows 7, you must be using Windows 7 Enterprise or Ultimate. If you have the Home edition of either, you’ll need to upgrade to use BitLocker.
In general, Windows 10 provides improved protection with BitLocker compared to Windows 7, and is easier to set up. In addition, some Windows 10 devices (and even some running Windows 8.1) come with full-drive encryption turned on by default, so if you have a newer computer that came with Windows 10 Professional or Enterprise pre-loaded, BitLocker may already be active. Some info and caveats about BitLocker, and Windows encryption in general, can be found here.
One tricky thing to remember is that not only do you need to be running one of the higher-end “professional” versions of Windows to use BitLocker, but you also need specific hardware: a Trusted Platform Module (TPM), which is a hardware-based method of storing encryption keys (most recent devices will already have this). Encryption without a TPM usually requires storing the encryption keys on the hard drive itself, which can be less secure. Again, it’s messy. The bottom line is that while you can use BitLocker without a TPM, it requires extra finagling (see below).
While a TPM can be added to some desktop motherboards, if your laptop doesn’t have one already, you’re probably out of luck. You can check to see by pressing Windows+R and then typing “tpm.msc.” If you have a TPM, you’ll get details; if not, you’ll get a message that a “Compatible TMP cannot be found.” More information about the TPM is available here.
Using BitLocker without a TPM requires a Group Policy change, which is possible by a non-administrator if you’re using a stand-alone PC not joined to a domain and are willing to edit local policy settings. For those who really want to wade into these waters, a walkthrough is available online.
The good news is that if you are running a Pro or Enterprise version of Windows, and if your laptop has a TPM, and if BitLocker is enabled, encryption of either your internal drive or an external storage device is fairly straightforward. The first thing to do is make a full backup first — just in case. Then, all you need to do is go into Windows Explorer, right-click the target drive and select the option, “Turn on BitLocker.” You then select a password, enable and save a recovery key (in case you lose or forget your password — otherwise, your data could be forever inaccessible), and select Encrypt entire drive. You will want to do this with your laptop fully charged and plugged in, and be forewarned — this can take a while. While a restart may be required, you can continue to use your computer while the encryption is progressing. You do want to make sure your laptop does not crash in the middle of encryption, so it’s best not to allow the process to be interrupted once it begins.
Step-by-step instructions can be found here, and a much more detailed overview about BitLocker under both Windows 10 and Windows 7 is available here.
While an encrypted drive is more secure, if you are asked at border control to log into your laptop and hand it over, and you comply, your encrypted drive is now unlocked and open for access. Keep any truly critical, proprietary or confidential information stored on an external USB or SDXC drive, encrypt the drive (using BitLocker, as described above), and keep the drive separate from the computer while traveling. That way, the only data on the local drive is information that you (and your company) don’t mind being seen.
If you have Microsoft Office files on your computer, you can individually encrypt them within Office using the Office “Protect Document” feature, and if you have BitLocker enabled, any file or folder can be individually encrypted. Even if you have device/drive encryption turned on, a separate encryption of critical files provides another layer of defense against unauthorized access.
5. Remove or pare back on social media
Speaking of data access, consider whether you are comfortable having border control staff view all of your contacts, emails and social media accounts, because they have the ability to request access to those as well — and sometimes do. One option is to remove all social media apps and browser bookmarks from your laptop before travel. (You will want to do the same for any iOS or Android devices.)
A second option is to create secondary accounts, containing only information needed for traveling, with no secure or confidential data. Alternative social media accounts are easy to create, and having a travel-only email account (with forwarding, as necessary, from existing accounts) is a quick task to set up on Outlook.com or Gmail. This also avoids the common problem of having proprietary information saved as email attachments in old emails that you may not even realize you have. If you keep a “clean” email account used only for traveling and wipe it after every trip, you can significantly reduce your exposure to releasing confidential data at the border or elsewhere on the road. If you want to take it one step further, create a new “travel only” Microsoft account, using a new email address created in Gmail or Outlook.com (and do not use the same password as your primary account).
You can then pare down your contacts list and calendars, if you have any that are considered confidential. Contacts can be selected and exported from Outlook.com or the Outlook desktop client, and imported into the new account as needed. Selected calendars can be shared between accounts for Outlook.
6. Use Windows To Go
Finally, for a higher level of security, Windows to Go allows the creation of an entirely self-contained Windows instance that can be installed to an encrypted USB drive and run on an otherwise empty “burner” laptop — either one carried while traveling or obtained while at the destination. This could avert needing to travel with a laptop at all, though it means you don’t have a device to use while on the plane. A number of third-party vendors offer secure Windows to Go options, or enterprise customers with Microsoft Software Assurance can create their own. For enterprise customers who are truly concerned about data security while traveling, Windows to Go is a worthwhile option.



 Microsoft
Microsoft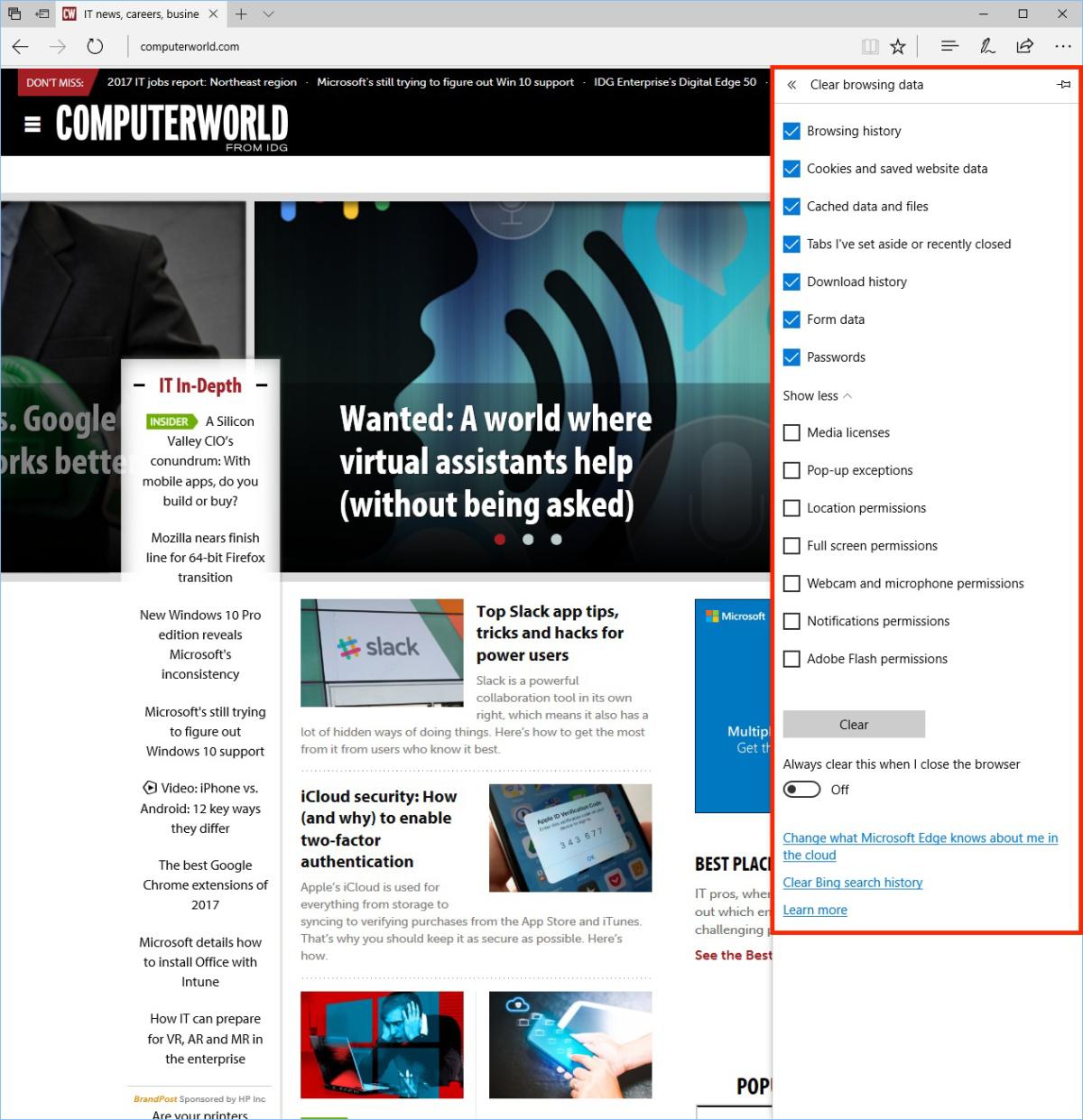 Richard Hoffman
Richard Hoffman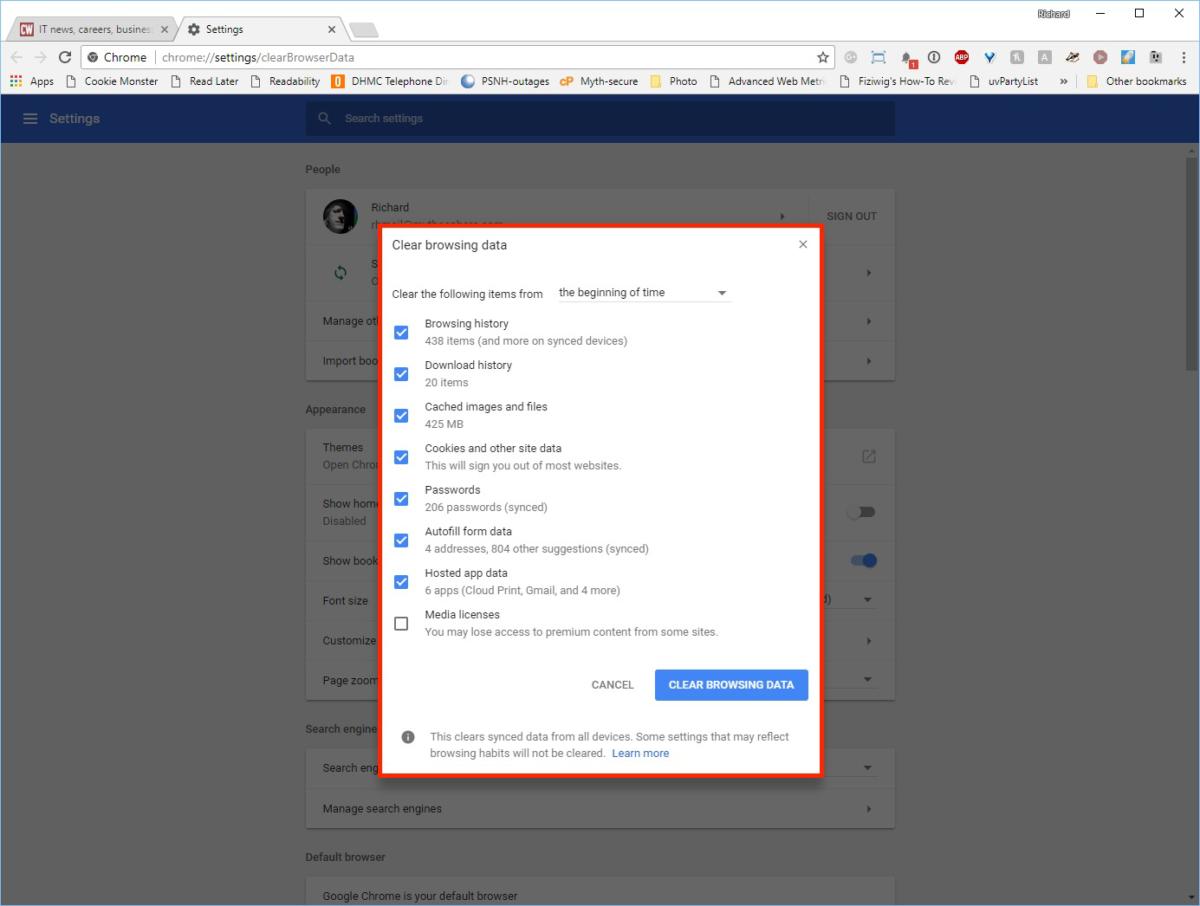 Richard Hoffman
Richard Hoffman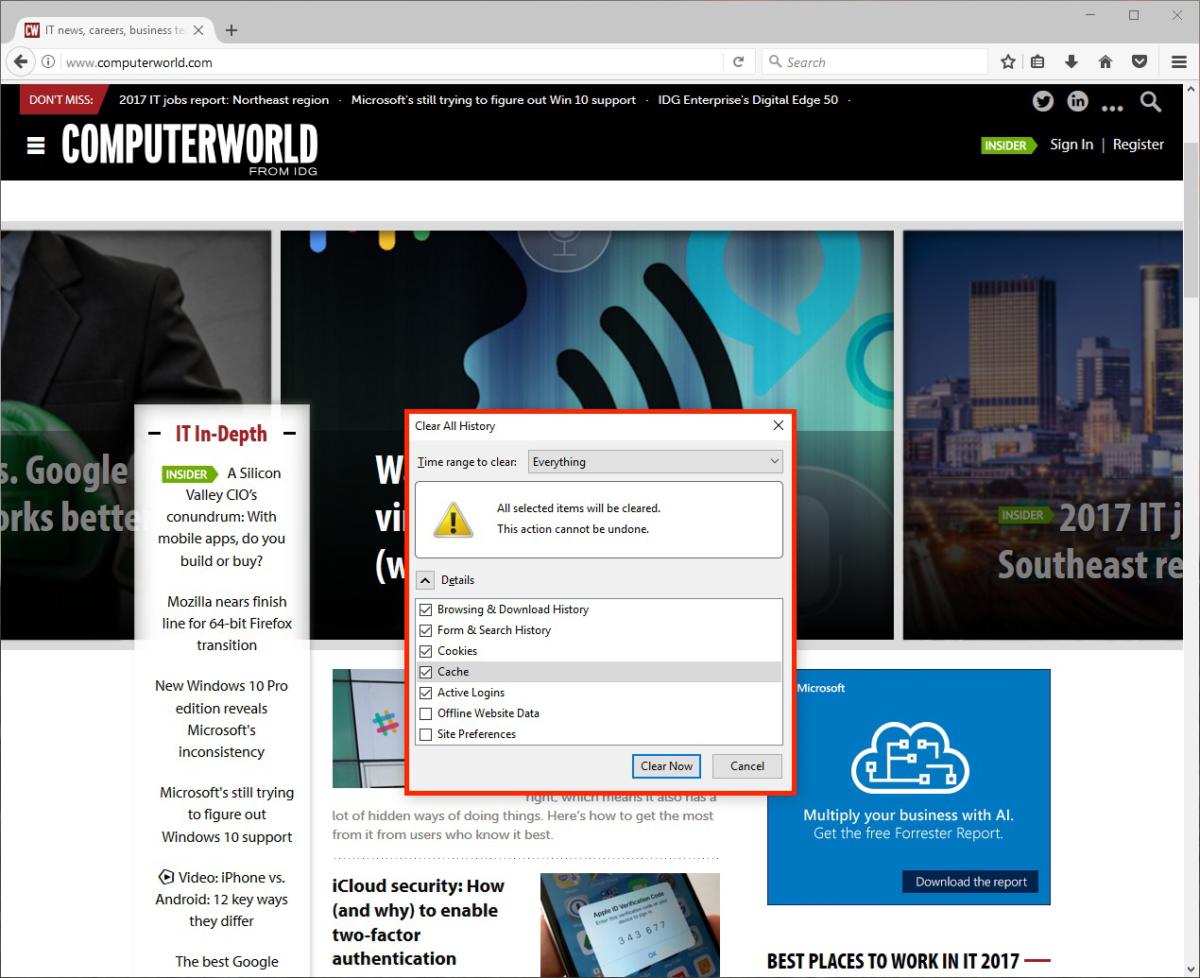 Richard Hoffman
Richard Hoffman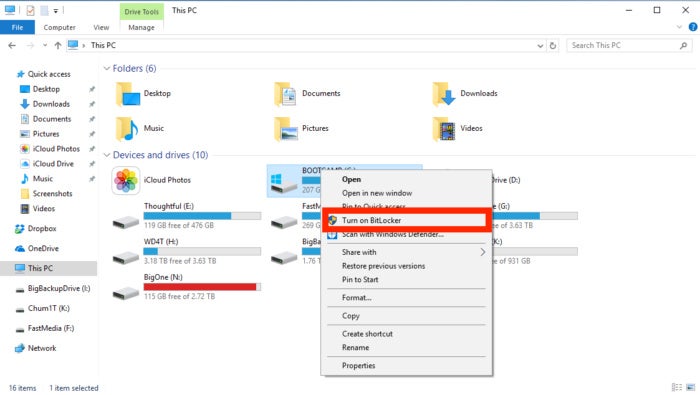 Microsoft
Microsoft